A man-in-the-middle attack is a type of eavesdropping attack, where attackers interrupt an existing conversation or data transfer. After inserting themselves in the "middle" of the transfer, the attackers pretend to be both legitimate participants. This enables an attacker to intercept information and data from either party while also sending.. What is a Man in the Middle (MitM) Attack? Une attaque de type "man-in-the-middle" (MitM) est une cybermenace de premier plan qui tire son nom du fait qu'un attaquant s'insère entre deux parties en communication. Si toutes les communications passent par l'attaquant avant d'arriver à destination, il est possible que l'attaquant supprime, lise ou modifie les messages avant qu'ils n'atteignent.

Attaque Man in the Middle (MITM)

ManInTheMiddleAttack Explained Effect Hacking

ManintheMiddle Attack Setup Download Scientific Diagram

¿Qué es un ataque ManintheMiddle (MITM)? Definición y prevención
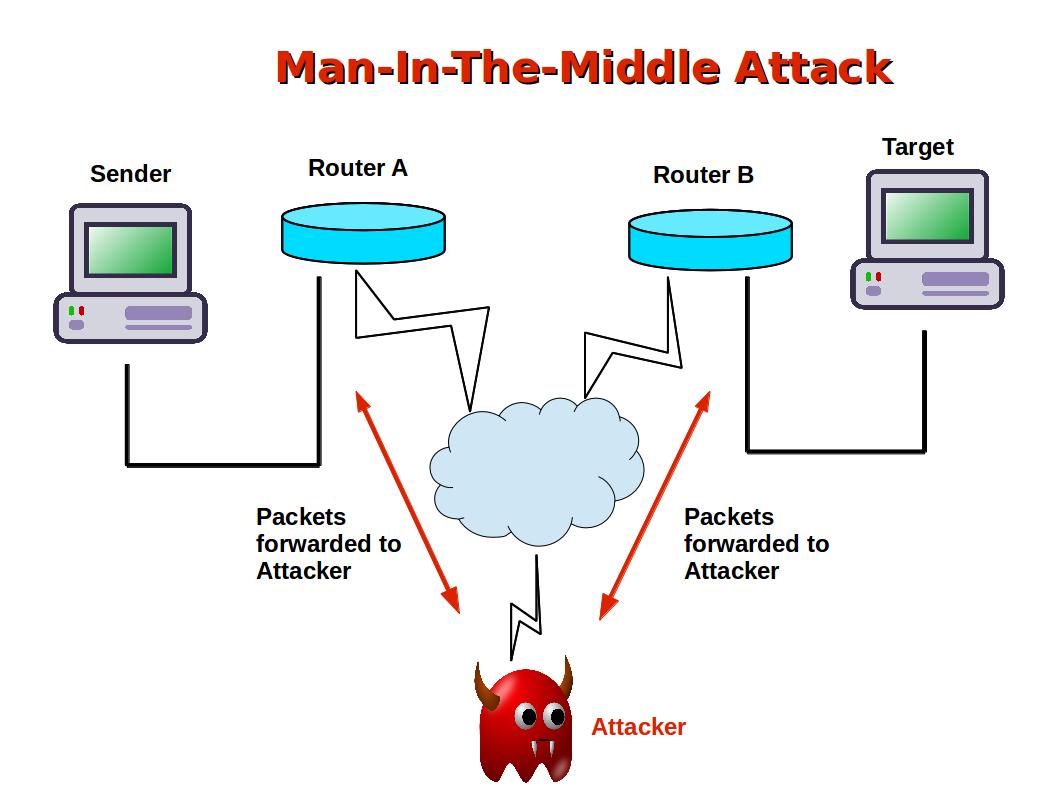
Computer Security and PGP What is a ManInTheMiddle Attack

Attaque Man in the Middle (MITM)

ManintheMiddle Attacks explained, defined
ManIntheMiddle Attack einfach erklärt + Tools / HTTPs
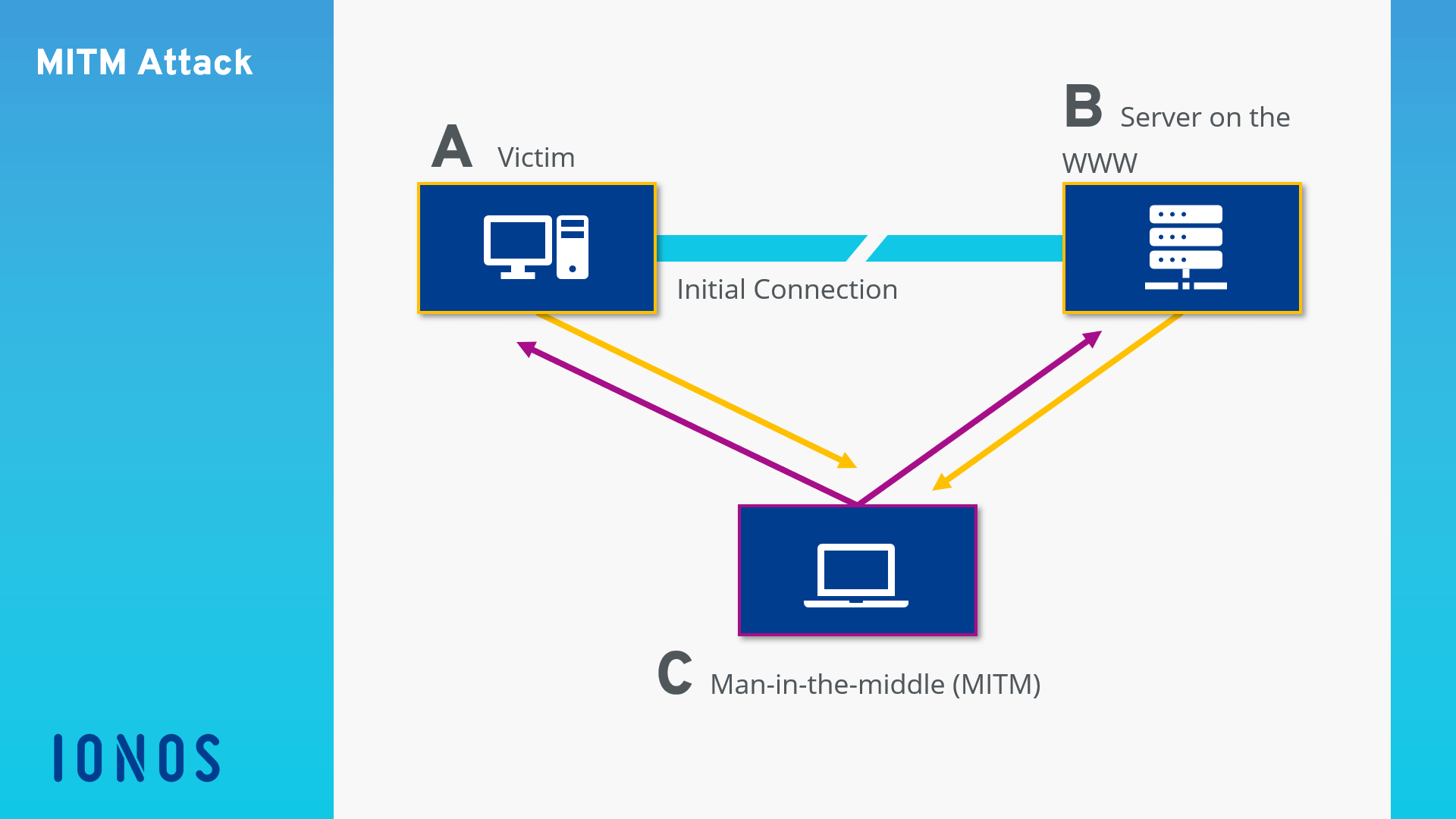
Maninthemiddle attack (MITM) Techniques & Prevention IONOS CA

Qu'estce qu'une attaque maninthemiddle (MITM)

Formas de ataques ManintheMiddle que existen y cómo mitigarlos
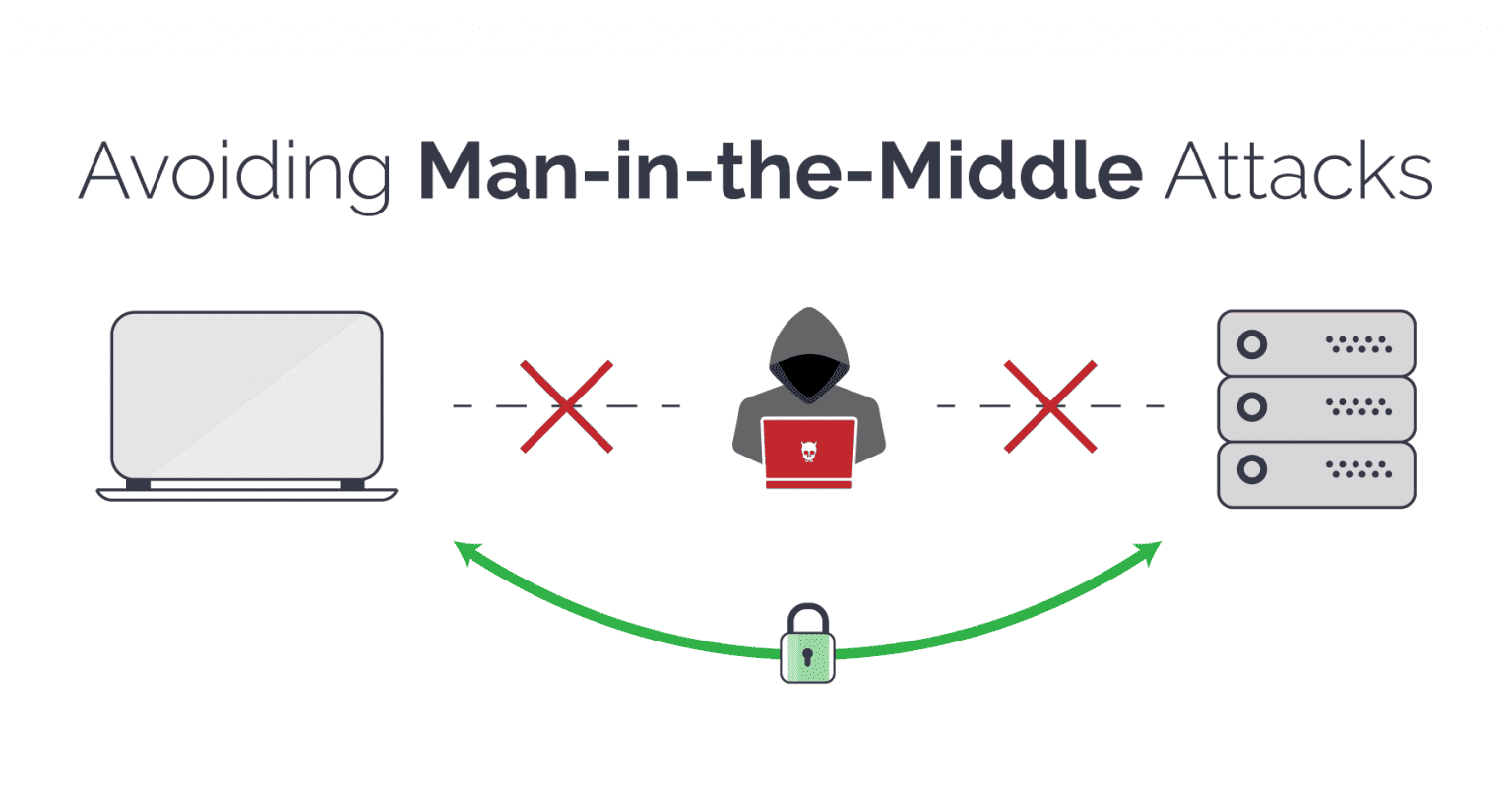
Maninthemiddle Attack How to Protect yourself Gadgetswright

What is Man in the Middle Attack? Types of Man in the Middle Attack

Attaque Man in the Middle (MITM)

Attaque Man in the Middle (MITM)

What is ManintheMiddle Attack MITM Attack Explained Edureka Cybersecurity Rewind 4
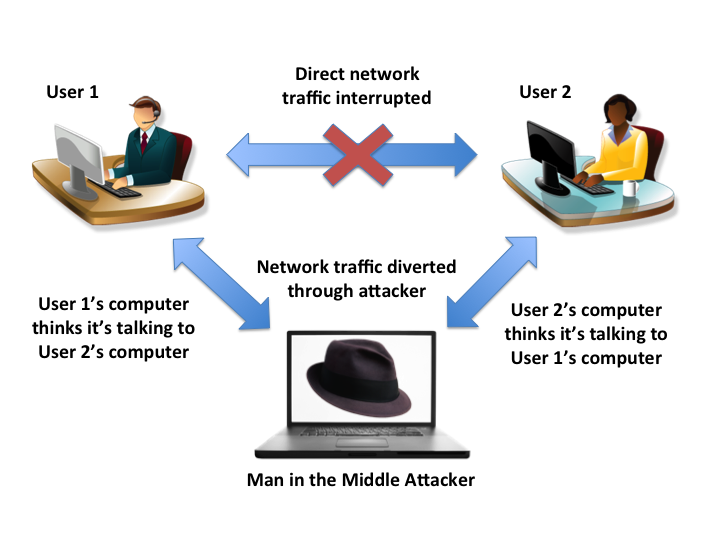
CS111 Winter 2013 Lecture 17 Introduction to Security

ManintheMiddle attack schematic Download Scientific Diagram

What is the ManInTheMiddle (MITM) attack? The Security Buddy
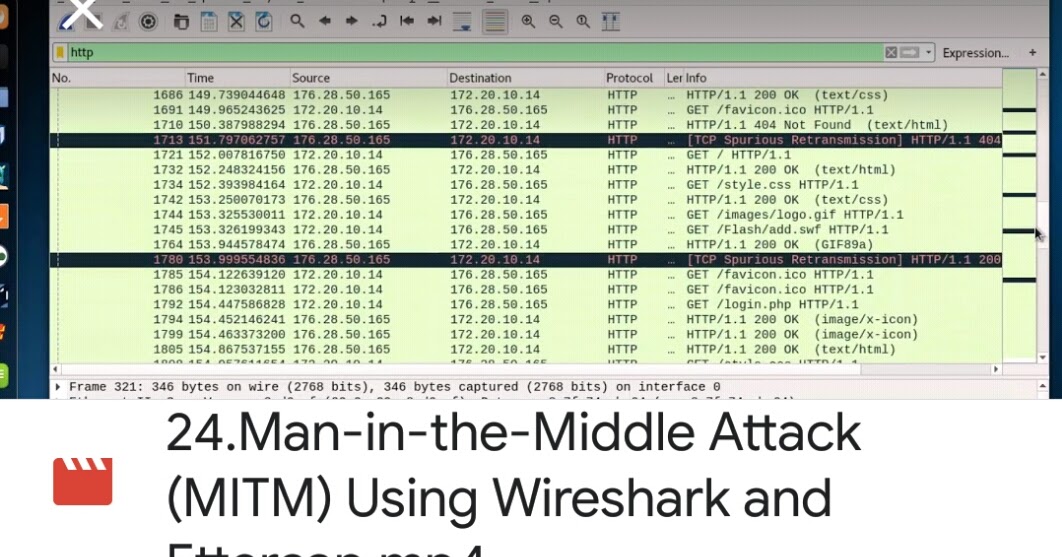
ManintheMiddle Attack (MITM) Using Wireshark and Ettercap
The Middle East has teetered on the edge of wider conflict since Hamas attacked Israel on Oct. 7, an attack Israel says killed 1,200 people and took another roughly 250 hostage. Israel's.. Man-in-the-middle attacks come in two forms, one that involves physical proximity to the intended target, and another that involves malicious software, or malware. This second form, like our fake bank example above, is also called a man-in-the-browser attack. Cybercriminals typically execute a man-in-the-middle attack in two phases.